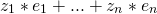FENTEC project provided the first fully-fledged functional encryption library. By fully-fledged we mean a library where the user can choose via an easy-to-use API between different schemes and each scheme can be instantiated from different cryptographic primitives.
FENTEC library actually comes in two flavors: GoFE is written in Go, while CiFEr is written in C.
What do we mean by choosing different schemes via an easy-to-use API? Well, functional encryption is a broad area and there are many schemes designed which serve for different purposes. Our libraries offer schemes for linear (also called inner-products) and quadratic polynomials. These can be single- or multi-client. Some offer a trusted key generation authority and some are decentralized which means no central trusted authority is needed. Also, our libraries offer schemes for attribute-based encryption.
These are a lot of new terms for almost anybody who is not a professional cryptographer. Let's try to explain at least some of them.
With inner-products we mean:
- Alice encrypts vector
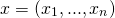
- Bob would like to know the value

- Central authority generates a functional encryption key for vector
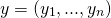 let's name it key_y.
let's name it key_y. - Central authority passes the key to Bob
- With key_y Bob can compute (decrypt) the value of
 (inner product of vector x and y). Bob knowns absolutely nothing about the vector x (except the inner product x * y)
(inner product of vector x and y). Bob knowns absolutely nothing about the vector x (except the inner product x * y)
This means Bob was not able to decrypt x, but only some "function" of vector 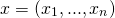 . This function is given by
. This function is given by 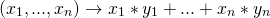
How do quadratic polynomial schemes differ from linear (inner-product) schemes? Well, the function in this case is quadratic, for example 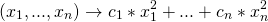
where 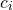 are some constants.
are some constants.
What does it mean single- or multi-client scheme? Let's check another example:
- Alice encrypts vector
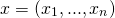
- John encrypts a vector
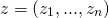
- Andrew encrypts a vector
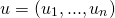
- Bob would like to know the value of
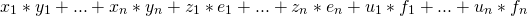
- Central authority generates a functional encryption key for a vector
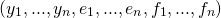 and passes it to Bob
and passes it to Bob -
Bob can now compute the value of
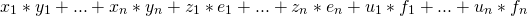 . Not only that he knows nothing about vectors x, z, u, he also does not know the values of:
. Not only that he knows nothing about vectors x, z, u, he also does not know the values of:
Bob only knows the value 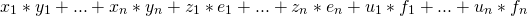 .
.
Lastly, decentralized schemes enable the generation of functional encryption keys without a central authority.
Attribute-based encryption schemes are slightly different kind of beasts. They provide functionality where a client can access or not access the decryption data of a ciphertext based on a set of attributes that he or she possesses.
At the beginning, we mentioned also different cryptographic primitives. As it turns out most practical functional encryption schemes are based either on modular arithmetic, pairings, or lattices. Implementation of functional encryptions schemes based on modular arithmetic is relatively straight-forward. On the other hand, the implementation of schemes based on pairings and lattices requires lower-level math artillery. Quite surprisingly all the required functionality for pairings is provided only by a handful of libraries. Furthermore, there is no fully-fledged library for lattice-based cryptography that could be easily reused. Therefore we provided a missing functionality for pairings in our fork of Barreto-Naehrig bilinear pairings implementation. Furthermore, in both, GoFE and CiFEr, we provide a wide variety of lattice primitives.
Functional encryption schemes enable various advanced real-world applications. For some examples please see FENTEC use cases . Perhaps surprisingly, these schemes also enable advanced machine learning models (like neural networks) on encrypted data - you might check a tiny demonstrator on our Github account.